
We are running Windows Virtual desktop, provisioned through marketplace, sometime in May 2019. I can only logon to the rdssessionhost with one user. Other users get´s the following error.
- Remote Desktop can’t connect to the remote computer for one of these reasons: 1) Remote access to the server is not enabled. 2) The remote computer is turned off. 3) The remote computer is not available on the network. Make sure the remote computer is turned on and connected to the network, and that remote access is enabled.
- @Hrishi, I think MS Remote Desktop 8.x used TLS 1.0 while MS Remote Desktop 10.x used TLS 1.2 to communicate to RD Gateway. Note: Apple, Microsoft, Google & Mozilla will end support for TLS 1.0 & TLS 1.1 starting March 2020.
- Enable Multimon using one of the three methods described below: a. Click “Use all monitors for the remote session” in the client (mstsc.exe) window. Use the “/multimon” switch on the mstsc.exe command line. Add “Use Multimon:i:1” to the RDP file. Connect to a computer running Windows 7 or Windows Server 2008 R2.
- However, users with a Mac downloaded Remote Desktop Connection 10 from the app store, and they receive the message stated in the title. It's similar to the Windows 10 issue, but I don't know how to fix it, as obviously the reg fix won't work.

I was having trouble creating an RDP client for Mac to a Windows Server. When I RDP to tha same Windows machine from another Windows machine everything worked as advertised.
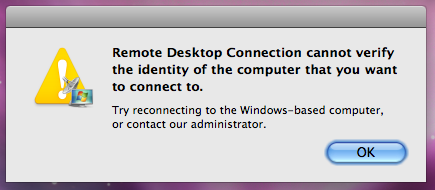
When I opened a RDP connection from my Mac to the Windows Server I would ge the following error: 'Remote Desktop Connection cannot verify the identity of the computer that you want to connect to'
Since I was able to connect from a Windows Machine I was under the assumption that the RDP problem layed with my Mac. Wrong!
Microsoft media player for windows 10 download. After trolling the internet for ages I finally found the fix.
Microsoft Remote Desktop 0x2407
How to fix the Mac OSX RDP Error:
On the Windows Server you are trying to RDP to perform the following
Ensure that RDP is enabled on the Windows Server and that the Firewall allows RDP.
Open the Management Console (mmc.exe)
Add the 'Local Computer Policy' snap-in
Goto: -> Computer Configuration -> Administrative Templates -> Windows Components -> Remote Desktop Services -> Remote Desktop Session Host -> SecurityChange the following two settings from their default (be aware that there might be a reason that MSFT has decided to set them to default. It might be advisable to revise those settings after a new Mac RDP client has been released)
'Require use of specific for remote desktop (RDP) connections' from 'Default' to 'Enabled', then select 'RDP' in the options pane
'Require user authentication for remote connections by using Network Level Authentications' to 'Disabled'
Restart the 'Remote Desktop Service' or simply restart the computer
Microsoft Remote Desktop 0x3000067 Mac
I was able to connect to various versions of Windows Server with this fix.
Credit -Microsoft Technet
TodayMicrosoft released a set of fixes for Remote Desktop Services that include twocritical Remote Code Execution (RCE) vulnerabilities, CVE-2019-1181 and CVE-2019-1182. Likethe previously-fixed ‘BlueKeep’ vulnerability (CVE-2019-0708), these two vulnerabilities are also ‘wormable’, meaning that anyfuture malware that exploits these could propagate from vulnerable computer tovulnerable computer without user interaction.
The affected versions of Windows are Windows 7 SP1, Windows Server 2008 R2 SP1, Windows Server 2012, Windows 8.1, Windows Server 2012 R2, and all supported versions of Windows 10, including server versions.
Windows XP, Windows Server 2003, and Windows Server 2008 are not affected, nor isthe Remote Desktop Protocol (RDP) itself affected.
These vulnerabilitieswere discovered by Microsoft during hardening of Remote Desktop Services aspart of our continual focus on strengthening the security of our products. Atthis time, we have no evidence that these vulnerabilities were known to anythird party.
It is important that affected systems are patched as quickly as possible because of the elevated risks associated with wormable vulnerabilities like these, and downloads for these can be found in the Microsoft Security Update Guide. Customers who have automatic updates enabled are automatically protected by these fixes. By default, Windows 10 Home and Windows 10 Pro users will be updated automatically.
Thereis partial mitigation on affected systems that have Network LevelAuthentication (NLA) enabled. The affected systems are mitigated against‘wormable’ malware or advanced malware threats that could exploit thevulnerability, as NLA requires authentication before the vulnerability can betriggered. However, affected systems are still vulnerable to Remote CodeExecution (RCE) exploitation if the attacker has valid credentials that can beused to successfully authenticate.
Microsoft Remote Desktop App
Resources
Links to downloads
Microsoft Remote Desktop Mac 0x204
SimonPope, Director of Incident Response, Microsoft Security Response Center (MSRC)